 We've been tricked, lied to, and quite possibly, bamboozled.
We've been tricked, lied to, and quite possibly, bamboozled. We've been tricked, lied to, and quite possibly, bamboozled.
We've been tricked, lied to, and quite possibly, bamboozled.
Who is the actual sender of this phishing email? (provide the email address)
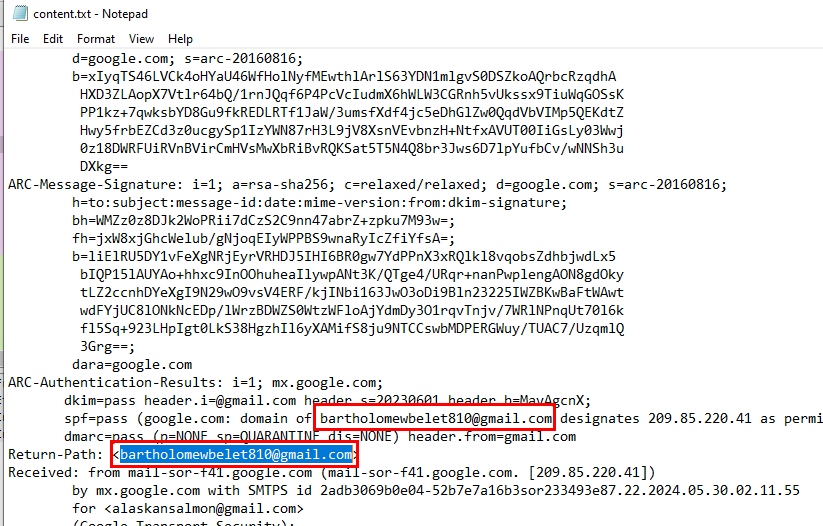
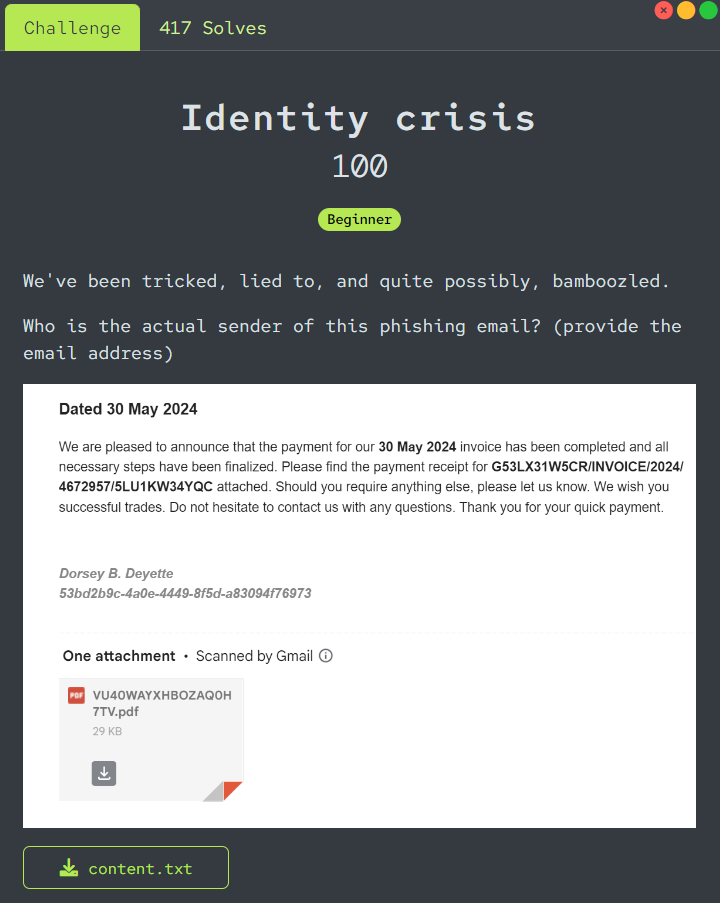
provided text file is actually eml file in disguised which mean it contains email header which should contain actual email sender in "Return-Path" as you can see right there
bartholomewbelet810@gmail.com
 I keep more than your skin safe. 😀
I keep more than your skin safe. 😀
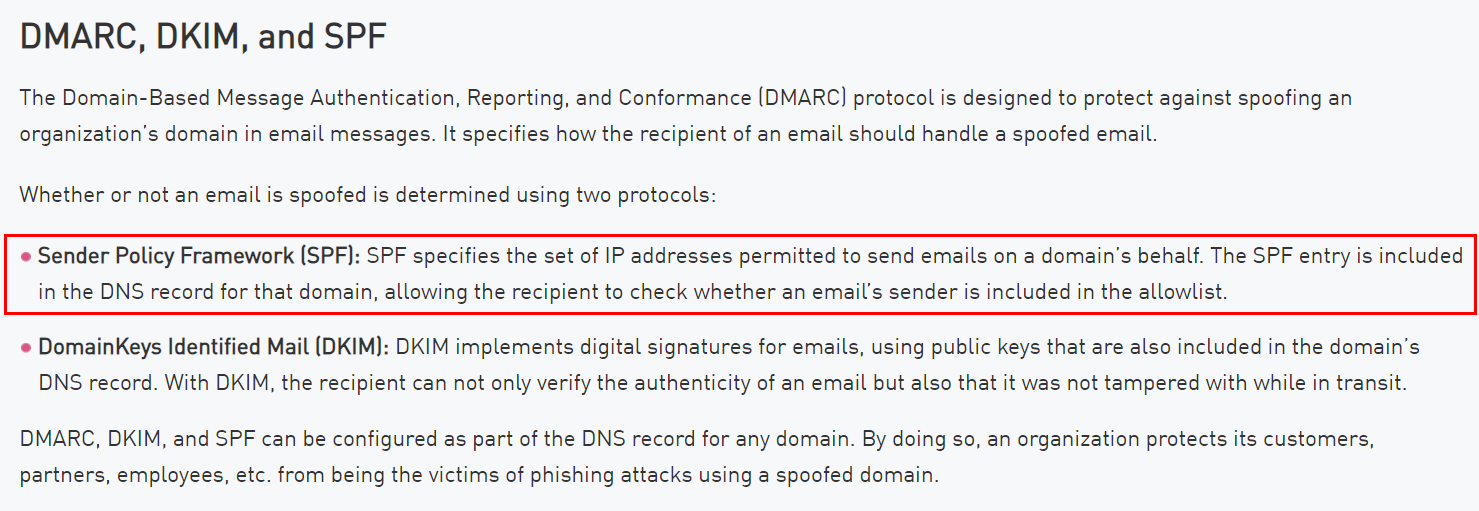 Well... This one is a well known protocol for email security
Well... This one is a well known protocol for email security
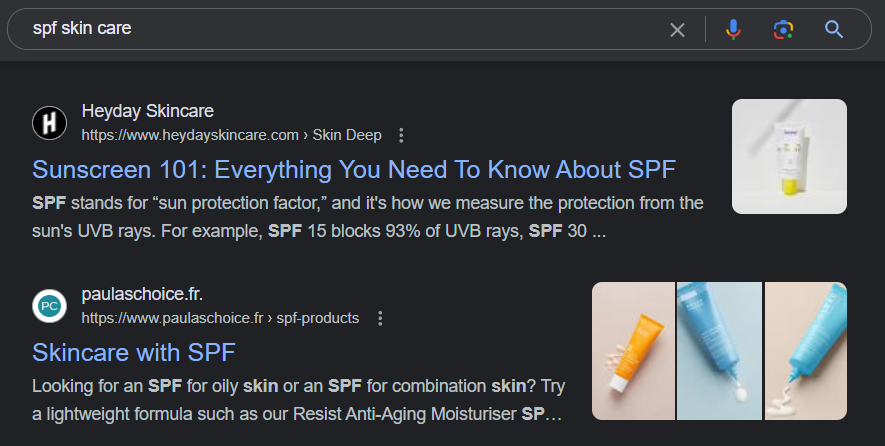
which has the same abbreviation as Sun Protection Skin which make challenge details made sense somehow
SPF
 A Goodcorp employee recently reported a phishing attempt to his company email address. We've provided the email headers for you to analyze. What country is the original sending server hosted in?
A Goodcorp employee recently reported a phishing attempt to his company email address. We've provided the email headers for you to analyze. What country is the original sending server hosted in?
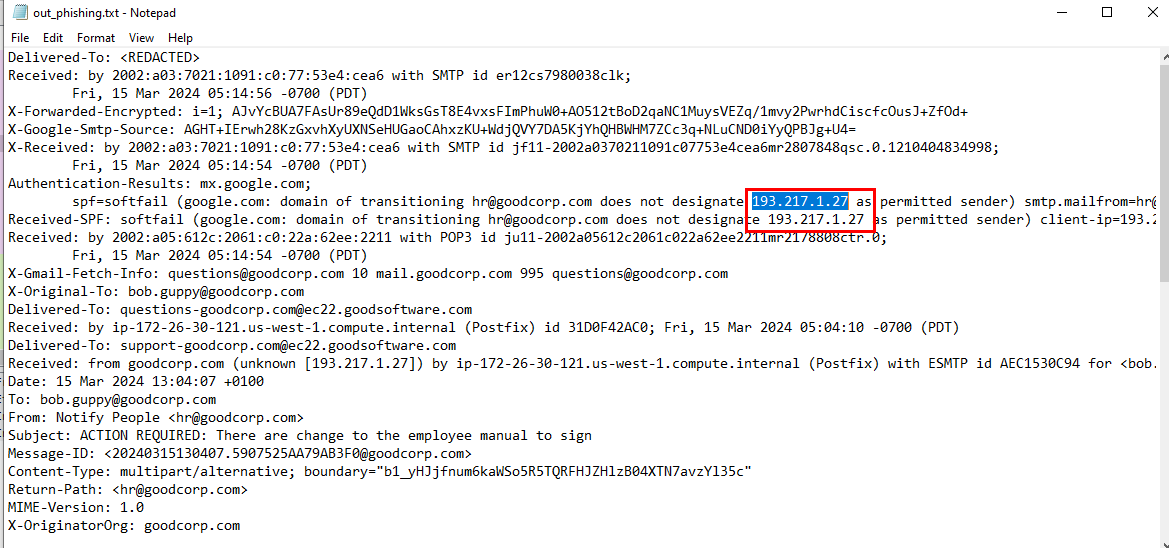
We got an eml file in disguised again, now we can acquire an SMTP address of an email sender right there
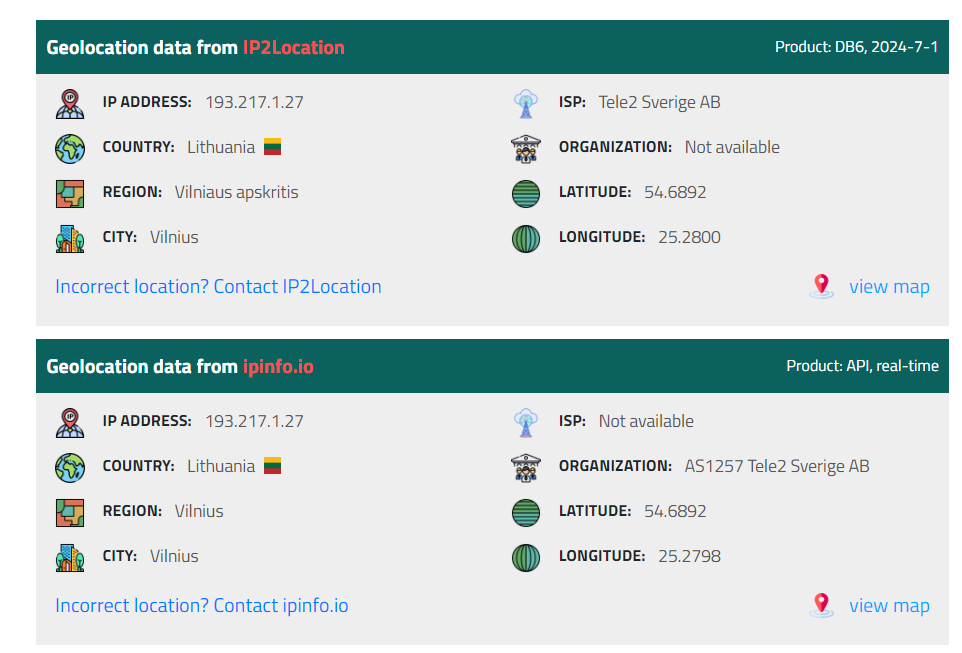
By using IPLocation or IP2Location API, we can see that this IP address is from Lithuania
Lithuania
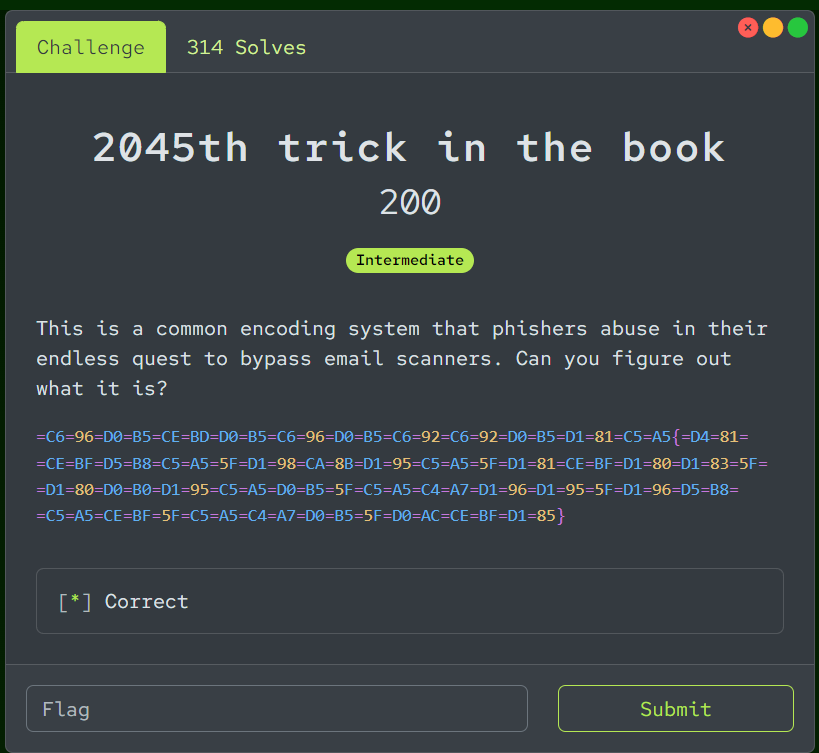 This is a common encoding system that phishers abuse in their endless quest to bypass email scanners. Can you figure out what it is?
This is a common encoding system that phishers abuse in their endless quest to bypass email scanners. Can you figure out what it is?
=C6=96=D0=B5=CE=BD=D0=B5=C6=96=D0=B5=C6=92=C6=92=D0=B5=D1=81=C5=A5{=D4=81= =CE=BF=D5=B8=C5=A5=5F=D1=98=CA=8B=D1=95=C5=A5=5F=D1=81=CE=BF=D1=80=D1=83=5F= =D1=80=D0=B0=D1=95=C5=A5=D0=B5=5F=C5=A5=C4=A7=D1=96=D1=95=5F=D1=96=D5=B8= =C5=A5=CE=BF=5F=C5=A5=C4=A7=D0=B5=5F=D0=AC=CE=BF=D1=85}
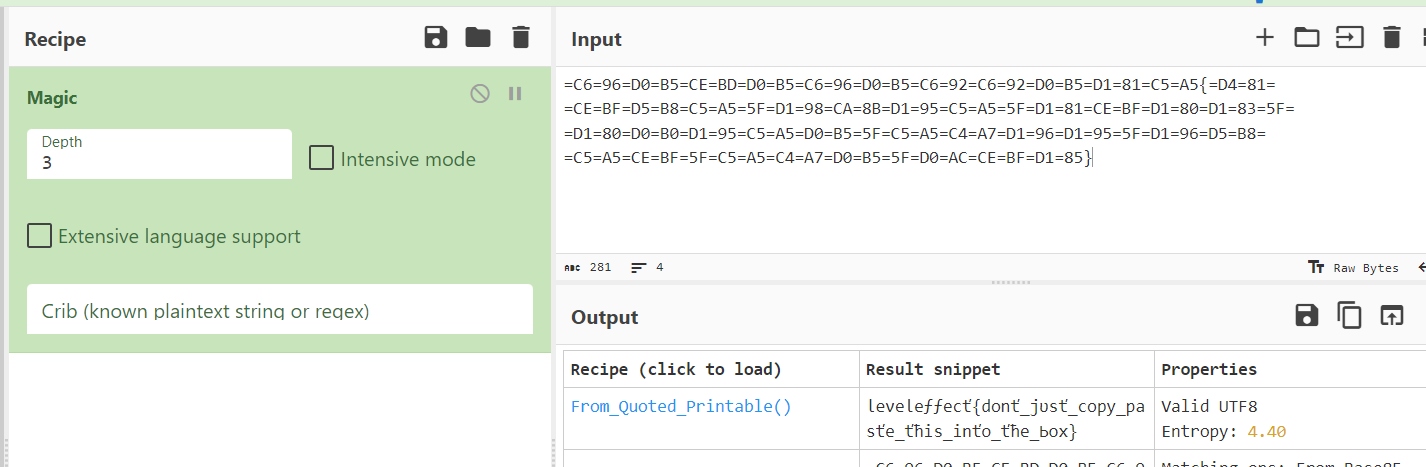
After let "Magic" on CyberChef recognized this format, we can see that its "Quoted printable" which can be used to bypass scanners and deliver phishing email to unfortunate users
Do not just copy an output from CyberChef to submit directly, we need to write it down again in plain english (UTF-8)
leveleffect{dont_just_copy_paste_this_into_the_box}